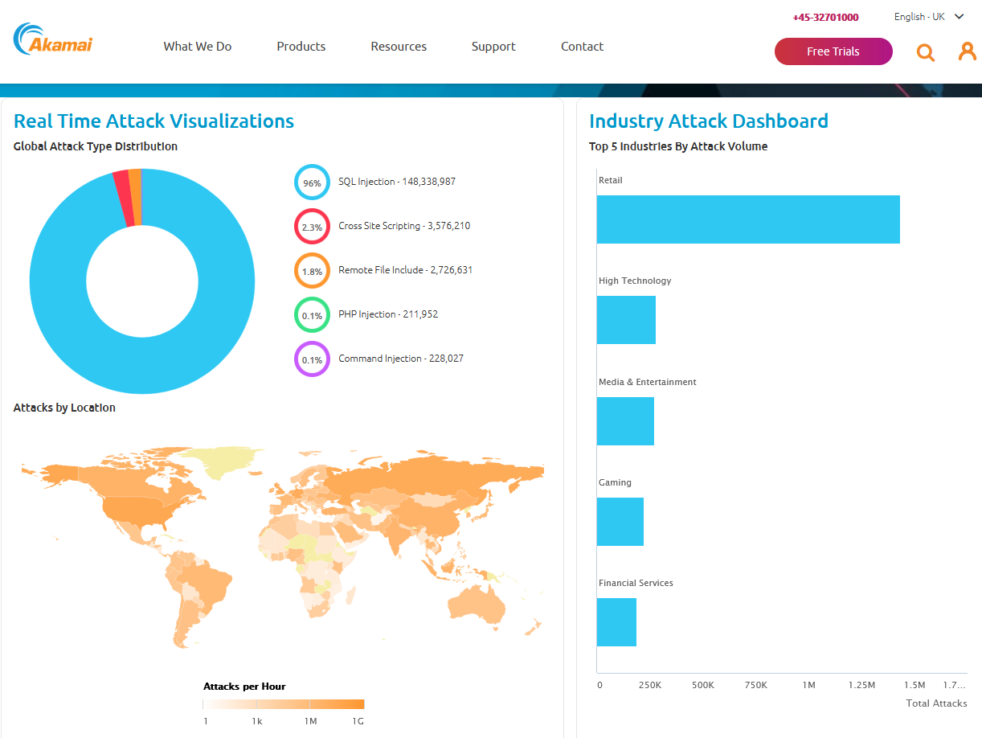
Why SQL Injection is Inexcusable
I found this awesome infographic from Akamai and I wanted to talk about it a bit because while the infographic itself is awesome, what is represents is the terrible truth behind the point I keep making about DevSecOps. More than 148 million SQL injection attacks… Why? Well, in short, because they work but they only… Continue reading Why SQL Injection is Inexcusable