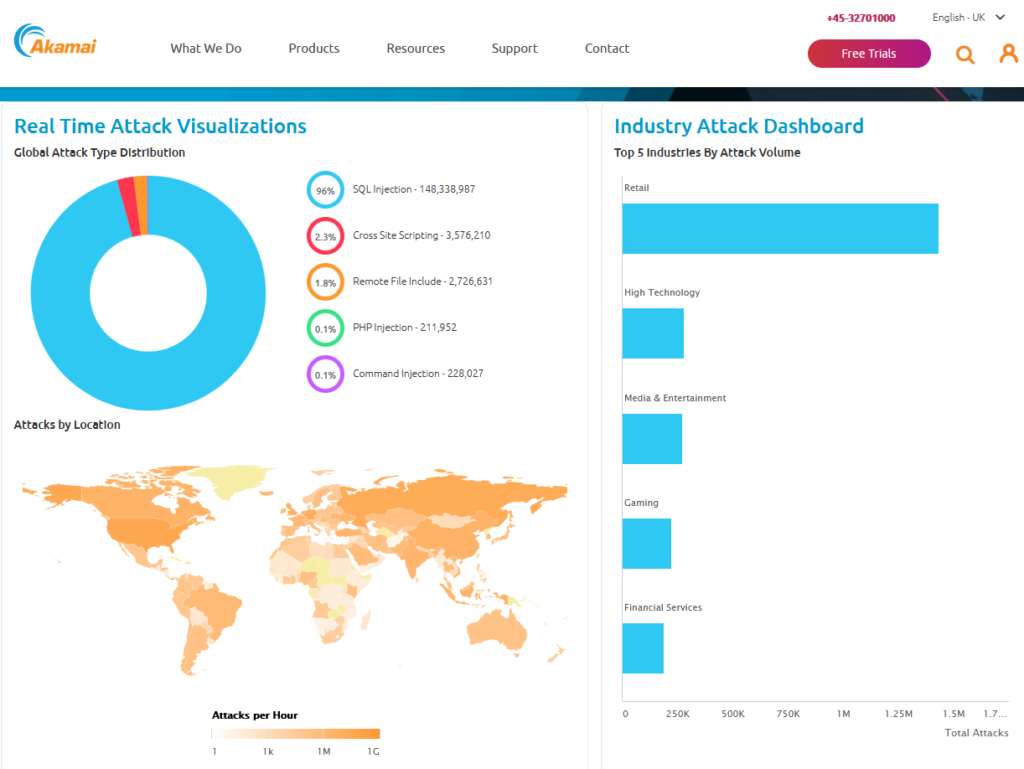
I found this awesome infographic from Akamai and I wanted to talk about it a bit because while the infographic itself is awesome, what is represents is the terrible truth behind the point I keep making about DevSecOps. More than 148 million SQL injection attacks… Why? Well, in short, because they work but they only work because of really crappy coding practices.
Preventing SQL injection attacks requires an extra 5 lines of code to sanitize the inputs for things like search boxes, address fields, etc. Most languages have the functions to do this built into the language. So why has this been on the OWASP top 10 list for more than decade? Crappy programming. I will post some examples below to show just how easy this is to do properly and you will see why this rouses my ire. It’s literally as simple as calling the function and then using the cleaned up version of the input. Doing this strips the ability to execute SQL queries right out of the input.
If software programmers were held to the same standard of product fitness for purpose as any other consumer good, most would fail miserably. The “reasonable person” standard for negligence ought to be applied to this and developers who don’t sanitize their inputs should be held financial and professionally liable for creating this crappy software. If cars (or anything else) were built this poorly, there would be massive litigation.
The current excuse that I hear a lot is that it was not included in the requirements documentation. So do the entire planet a favor and start specifying input sanitation as a functional requirement.
This is an example from PHP which is probably one of the most common and most poorly used programming languages on the entire Internet. It strips everything out of the SQL statement that would allow it actually successfully execute.
<?php $rawinut = ""CREATE USER 'root'@'my.ip.add.ress' IDENTIFIED BY 'MYPASSWORD'";"; $usethisinstead = filter_var ( $rawinput, FILTER_SANITIZE_STRING);echo $usethisinstead; // -> CREATE USER root@my.ip.add.ress IDENTIFIED BY MYPASSWORD ?>
This example is from Python, which is another very commonly used language on the internet. You can see how few lines it takes to clean up input.
import cgi
inlist = '"CREATE USER 'root'@'my.ip.add.ress' IDENTIFIED BY 'MYPASSWORD'";'
transform = cgi.escape(inlist)
print transform
My least favorite language of all time, Javascript. I know that a lot of your are going to say that Node.js, React, JQuery, etc. aren’t really Javascript and have their own calls. That is true. They just don’t get used either. This one is plain vanilla JS but versions of it exist for Node, React, JQuery and almost every other framework out there.
<script type="text/javascript" src="dist/purify.min.js"></script> <script type="text/javascript"> var clean = DOMPurify.sanitize(dirty); </script>
Remember when I said it was 5 lines or less…. That was not an exaggeration. That’s all it takes to make most SQL Injections a thing of the past.
